This is why it’s good to put your software to the cybersecurity test!
March 1, 2025
CTF Write-Up: Authenticated Defacement via Permalink Collision
Overview
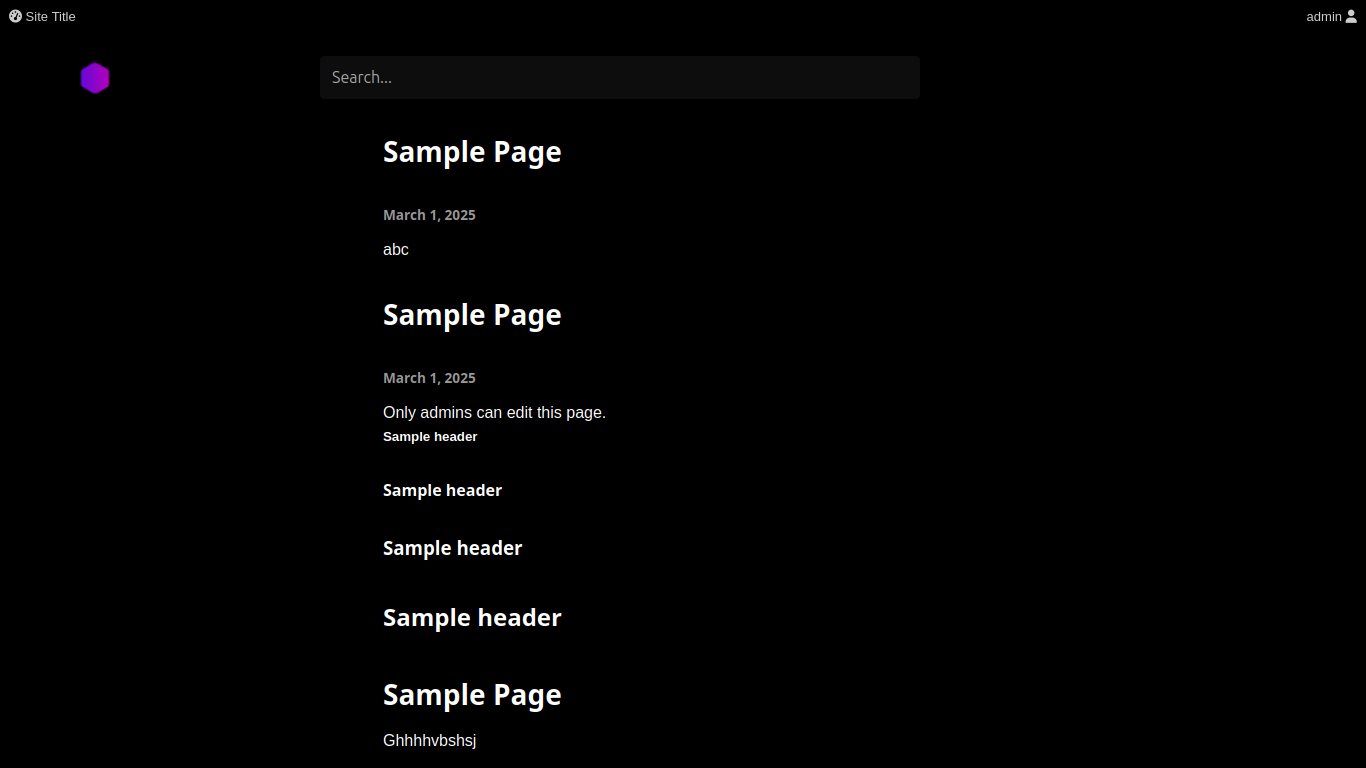
As part of testing my own Capture the Flag (CTF) challenge at ctf-instance.wlphosting.com, I discovered a vulnerability in a web application’s role-based access controls. This issue allowed authenticated users with Contributor permissions to deface public pages by exploiting a flaw in permalink handling.
This is exactly why it’s so important to put new software through rigorous cybersecurity testing before launch. By identifying these kinds of issues early, we can fix them before they become real-world problems. Plus, my CTF acts as an open bug bounty — I actively encourage others to start playing with it and report bugs, and I offer rewards for valid findings.
Vulnerability Details
Type: Authenticated Defacement
Pre-requisites: Logged-in Contributor account
Technical Breakdown:
- The application uses multiple user roles (Administrator, Editor, Contributor, Subscriber).
- Contributors should only be able to create and submit drafts for approval.
- By creating a draft with the same permalink (URL slug) as an existing published page, my draft content was displayed on the live site, replacing the original published content.
This issue arises from improper handling of permalink collisions, leading to unauthorized defacement of live pages.
Impact
Although this defacement requires an authenticated session, it exposes the risk of insider threats and misconfigured access control. It disrupts content integrity by allowing unapproved changes to live content.
Mitigation
The issue has been hot-fixed, and a permanent solution to manage duplicate permalinks and enforce stricter role-based permissions is in progress.
Takeaways
- Enforce Proper Role Validation: Ensure Contributors can’t impact published content.
- Resolve Permalink Collisions: Prevent draft content from overriding live pages.
- Test for Insider Threats: Simulate real-world scenarios for different user roles.
If you’re into cybersecurity and want to sharpen your skills, check out ctf-instance.wlphosting.com. It’s a great opportunity to learn, test, and even earn rewards for your discoveries. Stay curious and keep testing!
